Category: Security
-
Tor Onion Farming in 2021
(Read more...)Around four years ago, I wrote a blog post about creating vanity
.oniondomains for Tor. To recap,.oniondomains are special domains understood by Tor, and when visiting these sites, traffic never leaves the Tor network and is end-to-end encrypted, just as if you were to use HTTPS. Furthermore, the server’s identity is completely protected, if you are into that sort of thing. Also, the domain name is linked to the server’s public key fingerprint, and so knowing the.oniondomain is sufficient to authenticate the server and preventing any MITM attacks or certificate authority compromises that could happen with HTTPS.Recently, I decided that my password generator
correcthorse.pw(GitHub) should also have a vanity onion domain, and naturally, I decided to generate some onions. -
Online Judging Sandbox: From Linux to FreeBSD
(Read more...)As most probably know, DMOJ uses a sandbox to protect itself from potentially malicious user submissions. An overview of the Linux sandbox has been published by my friend Tudor. However, it doesn’t go deep into the implementation details, many of which differ between Linux and FreeBSD.
At its core, the sandbox,
cptbox, uses theptrace(2)API to intercept system calls before and after they are executed, denying access and manipulating results. The core is written in C, hence the namecptbox.Perhaps the most obvious difference between Linux and FreeBSD is that on Linux,
ptrace(2)subfunctions are invoked asptrace(PTRACE_*), while on FreeBSD, it isptrace(PT_*). But this difference is rather superficial compared to the significant internal differences. -
Onion Sites
(Read more...)I am probably somewhat obsessed with having my websites accessible over a
.oniondomain, perhaps because I like vanity names (I’ll explain this later).A while ago, I introduced
dmojsites2fpbeve.onionfor DMOJ. And today, I introducequantum2l7xnxwtb.onionfor this website.These .onion websites are accessible over Tor, and do not ever leave the Tor network when accessed this way. Despite not having HTTPS (which is basically unattainable due to the lack of any certificate authority willing to issue free certificates for .onion), the encryption is end-to-end: only your computer and the server at my end can see the actual traffic in plaintext. For those familiar with the Tor network, there is no exit node which can watch your traffic in this setup.
To preview these websites, you can use tor2web.org. In practice, you simply have to append
.linkafter any.oniondomain, and tor2web will take care of the rest. For example,quantum2l7xnxwtb.onioncan be accessed asquantum2l7xnxwtb.onion.link. Note that you lose pretty much all the benefits of Tor this way..onion domain names are composed of 16 “random” alphanumeric characters (more precisely, matching
^[a-z2-7]{16}\.onion$). These are derived from the public key of the onion site. Now, you may have noticed that the DMOJ and Quantum onion sites have a nice, identifiable prefix. This is called a vanity name. To generate these, we perform the equivalent of generating keys until we happen to get the desired prefix. This process is not too fast, as you can probably imagine. -
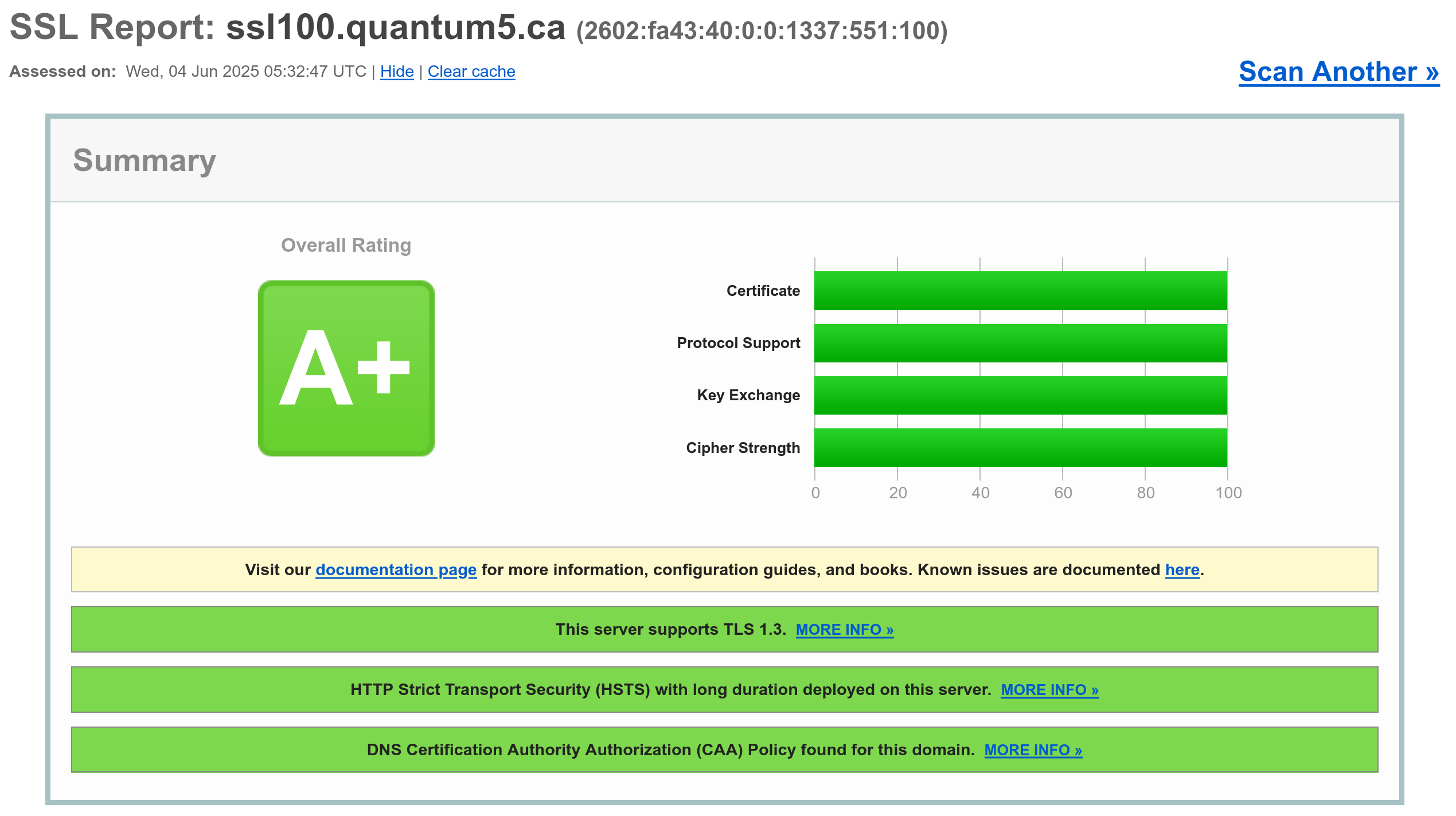
Getting a perfect score on the SSL Labs Server Test
(Read more...)I decided to take it as a challenge to get a full perfect score on the de facto standard of SSL implementation quality, the Qualys SSL Labs Server Test.
Update (2025-06-04): changed the domain name and modernized configuration.
Needless to say, getting a perfect score is not without cost. For example, many browsers will be incapable of accessing the site. For this reason, I decided to use a separate domain name: ssl100.quantum5.ca, which also runs on a separate IPv6 address to prevent any contamination on this website (there is no IPv4 since addresses are expensive), so you will need IPv6 access.